Volume 12, Issue 3 (Summer 2024)
PCP 2024, 12(3): 217-230 |
Back to browse issues page
Download citation:
BibTeX | RIS | EndNote | Medlars | ProCite | Reference Manager | RefWorks
Send citation to:



BibTeX | RIS | EndNote | Medlars | ProCite | Reference Manager | RefWorks
Send citation to:
Gholamrezaei H, Falsafinejad M R, Khodabakhshi-Koolaee A. Exploring the Dimensions of Online Child Sexual Abuse: A Qualitative Meta-synthesis Study. PCP 2024; 12 (3) :217-230
URL: http://jpcp.uswr.ac.ir/article-1-924-en.html
URL: http://jpcp.uswr.ac.ir/article-1-924-en.html
1- Department of Counseling, Faculty of Humanities and Social Sciences, North Tehran Branch, Islamic Azad University, Tehran, Iran.
2- Department of Assessment and Measurement, Faculty of Psychology and Educational Sciences, Allameh Tabataba’i University, Tehran, Iran ,falsafinejad@yahoo.co.uk
3- Department of Psychology and Educational Sciences, Faculty of Humanities, Khatam University, Tehran, Iran.
2- Department of Assessment and Measurement, Faculty of Psychology and Educational Sciences, Allameh Tabataba’i University, Tehran, Iran ,
3- Department of Psychology and Educational Sciences, Faculty of Humanities, Khatam University, Tehran, Iran.
Full-Text [PDF 922 kb]
(1435 Downloads)
| Abstract (HTML) (2538 Views)
Full-Text: (1494 Views)
Introduction
The rapid development of communication technologies, along with the widespread use of the Internet, has fundamentally transformed almost every part of human life, including work, health, education, communication, and entertainment, to the extent that these technologies have become a common basic need for human daily life due to their relatively low cost and easy access (Cikman et al., 2017). With the widespread use of the Internet, commercial sites that contain pornographic content, chat rooms, and uncontrolled communication networks serve as platforms that connect children with pedophiles, thereby promoting potential online sexual abuse (Keçe, 2018). Sex offenders often use the Internet to communicate with children to facilitate in-person sexual abuse or to create and distribute sexual images of children (Dimitropoulos et al., 2022). Online child sexual abuse includes displaying, collecting, compiling, and distributing child sexual abuse content for personal sexual gratification, financial gain, interaction with other pedophiles, participation in online live streams of child sexual abuse, and grooming to encourage children to engage in sexual acts online and then offline and in reality (Özçalık & Atakoğlu, 2021; Açar, 2017). Child grooming refers to a relationship based on trust between a minor and an adult who uses information and communication technologies to solicit and exploit young people to provide online and offline child sexual abuse acts (Kloess et al., 2014).
Child sexual abuse material has become a big problem in the 21st century, and despite the increased awareness and efforts of governments and non-governmental organizations in the private sector, still alarming statistics exist in this field. In 1998, the US National Center for Missing and Exploited Children identified online sexual abuse as a new form of child sexual abuse. In the following year, 9 673 reports were received by this center, and in 2021, these reports reached >29 million reports, of which 99% were related to online child sexual abuse, indicating a three-thousand-fold increase over the past 22 years (IWF, 2020). Sex offenders often use the Internet to communicate with children to facilitate in-person sexual abuse or to create and distribute sexual images of children (Dimitropoulos et al., 2022). Online sexual solicitation (OSS) of children occurs when an adult stranger uses the Internet to access, interact, and establish relationships with children to induce them to engage in sexual conversations and acts, offline and/or online. Online sexual solicitation may involve a variety of sexually explicit acts, desired or undesired by the child, such as initiating conversations of a sexual nature (e.g. cybersex, describing sexual acts, and exchanging sexual information), exchanging pornographic images, and meeting offline and engaging in sexual acts (Gemara et al., 2022). Various studies have addressed the effect of experiencing physical abuse, sexual and emotional abuse, and physical and emotional neglect in children in the etiology of mental disorders in children (McNally et al., 2021; McKay et al., 2021; Marshall et al., 2020) and have shown that many factors, including cyberspace and its widespread use, are effective in the phenomenology of child abuse (Drăgan, 2018). However, the reported cases of child sexual abuse are like the tip of the iceberg as the exact rate of sexual abuse is not stated in detail. For example, Abbas and Jabeen (2020) showed that 44% of the men and 39% of the women participating in the study reported that they have experienced at least one form of sexual abuse (looking at private parts, pornography, touching private parts, talking sexually and or having sex) in childhood.
As stated earlier, online child abuse has been addressed by many studies conducted in the last few years. Since children start using the Internet at a young age and for a long time, they are at risk of engaging in online sexual abuse and these online threats pose a potentially growing problem to the mental health of the community, leading to a dramatic increase in child abuse reports. Accordingly, the Internet Watch Foundation (IWF), a UK-based NGO, identified >153,000 new web pages containing child sexual abuse images in 2020, showing a 16% increase compared to 2019 (IWF, 2020). In the UK in 2016, 100000 people were involved in online sexual abuse, and 5%-25% of children in Europe and the US experienced sexual abuse, viewed pornography, and became involved in online sexual abuse. Moreover, from 2009 to 2013, four thousand child victims of sexual abuse were identified by the Interpol (Carr, 2020). Acar also reported that during 10 weeks, more than a thousand different people offered money to a virtual Filipino child named Sweetie, so that in exchange for receiving this money, he would send them online sexual images of himself. Landberg et al. (2022) showed that 27.5% of high school students, including 40.5% of females and 12.8% of males in Sweden with an average age of 18 have engaged in online sex or been forced to do so in the past year.
Thus, it is essential to raise the awareness of parents, psychologists, counselors, teachers, and all health professionals dealing with children and families about online child sexual abuse. To this end, this systematic review study seeks to review the studies conducted in this field to reveal the dimensions of online child sexual abuse highlighted in the literature in recent years. The insights from this study can contribute to developing child sexual abuse prevention and training programs.
Materials and Methods
Using a systematic review approach, the present study was conducted to analyze studies that addressed online child sexual abuse. Systematic review is a standard approach to examining the questions and findings of several studies (Boland et al., 2014). A systematic review is an explicit method to identify, evaluate, and analyze the previous work done by researchers and scholars (Okoli & Schabram, 2010). Studies that can be evaluated using a systematic review should be published online and present field and empirical findings. Thus, the research setting includes all valid scientific articles addressing online child sexual abuse. Since sexual abuse on online platforms has increased in recent years, all the selected articles were conducted within this time frame (2014-2023). The required data were collected using a researcher-made worksheet form. The identified scientific documents and records were categorized using content analysis. The collected data were analyzed using open, axial, and selective coding and Wright et al.’s seven-step model (Wright et al., 2007). To assess the reliability of the coding scheme, the data were re-coded by four raters using Scott’s method. The inter-rater agreement was estimated as 0.74, showing a 74% agreement between the raters (Equation 1).
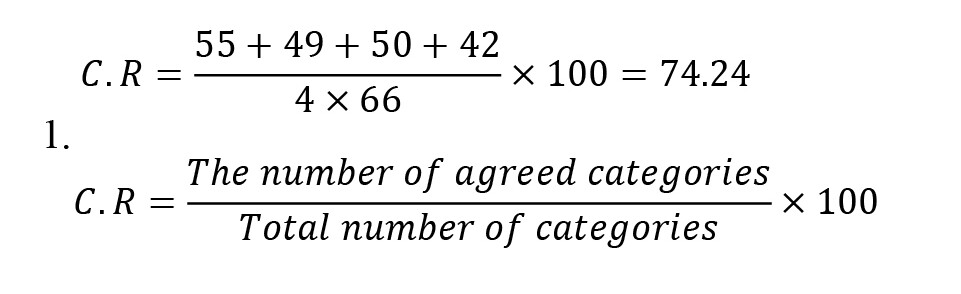
This study was conducted through five steps as detailed below:
Step 1: Developing the research question
Table 1 presents the research questions.
Step 2: Formulating the research protocol
To reduce any probable bias, the review protocol was developed before retrieving the related records. To collect the data, we developed a set of criteria to select and categorize the articles (Moffet, 2015).
A. The inclusion criteria used in this study included:
1. The articles that addressed learners’ online sexual abuse
2. The articles that reported adequate data (the sum of data or information required to create an influential contention or back a specific conclusion) on online child sexual abuse
3. The full-text articles that were reviewed by subject-matter experts and published online
B. The exclusion criteria used in this study included:
1. The articles that did not report enough data about online child sexual abuse or the articles that only assessed the relationship between online child sexual abuse and other variables quantitatively
2. The articles lacked scientific rigor and were published in low-quality journals and conferences without an international index or reported impact factor.
3. The articles that were not published in the intended time frame (2014-2023). In other words, the articles that were published before 2014 and their results were no longer useful for current issues.
Step 3: Search strategy
The intended articles were searched using the search strategy proposed by Prashar (2015). To this end, all valid scholarly articles were searched using the keywords “child sexual abuse”, “online child sexual abuse”, and “cyber sexual abuse” in domestic databases, such as Google, SID, Normagas, Magiram, Comprehensive Humanities Portal, Iranian Research Institute for Information Science and Technology (IranDoc), and Elmnet Search Engine as well as international databases including Scopus, Emerald, Sage, Scientific Information Database, Science Direct, ProQuest, Springlink, World Scientific, Taylor & Francis, Google Scholar, Eric, and Wiley. The records related to the objectives of the study were retained and unrelated records were removed. Furthermore, Google Scholar and related websites, such as Child Abuse & Neglect were searched manually to identify the gray literature. To improve the rigor of the results, the databases were searched separately by two experts who were familiar with search methods and information sources. Moreover, three experts in the field of online platforms and psychology monitored the search protocol. The data in this study were collected from scholarly and research articles published in national and international databases. The articles have been published using strict review protocols in reputed journals.
Step 4: Extracting articles
A standard form was used to record the intended information, including the source (journal name, article title, and author(s)), purpose (the objective(s) of the study), methodology, and results. The data were collected by searching the intended keywords in the databases. Considering the inclusion criteria, 113 articles published in English and Persian were identified. After reviewing the articles based on the exclusion criteria, the irrelevant articles were excluded and finally, 22 articles were used for the final review. Table 2 presents the search strategy used in this study.
Step 5: Quality assessment
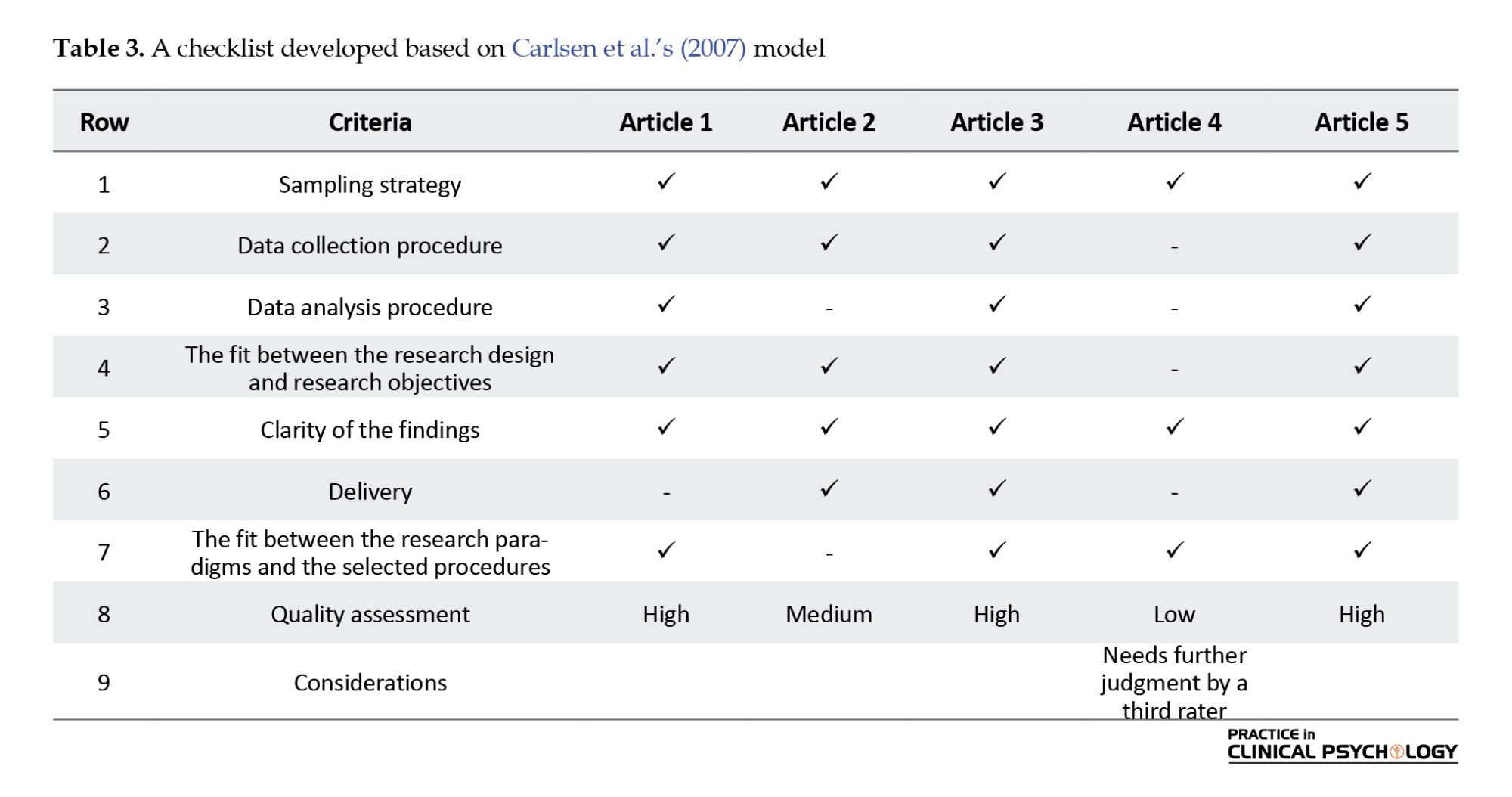
Every study, including qualitative studies and systematic reviews, must have acceptable validity and objectivity. In systematic review studies, a comprehensive search will lead to finding a lot of relevant studies, but since all these studies are not of adequate and acceptable quality, before the review, the extracted records should be selected following the inclusion and exclusion criteria. Before entering the analysis, each article should be analyzed using suitable tools and based on defined criteria, and only articles that have acceptable quality should be analyzed and reviewed. A checklist was used in this study to specify the high, medium, and low quality of the selected articles. To this end, the selected articles were scored and those with lower scores were excluded. Table 3 presents a rating checklist developed based on Carlsen et al.’s model (Carlsen et al., 2008).
The extracted articles were reviewed and rated independently by at least two raters using the criteria detailed in Table 3. The raters specified the reasons to reject an article. However, in the case of any disagreement between the two raters, the article would be reviewed and assessed by a third rater.
Results
Data analysis was performed using Wright et al.’s seven-step model (Wright et al., 2007).
Step 6: Data analysis
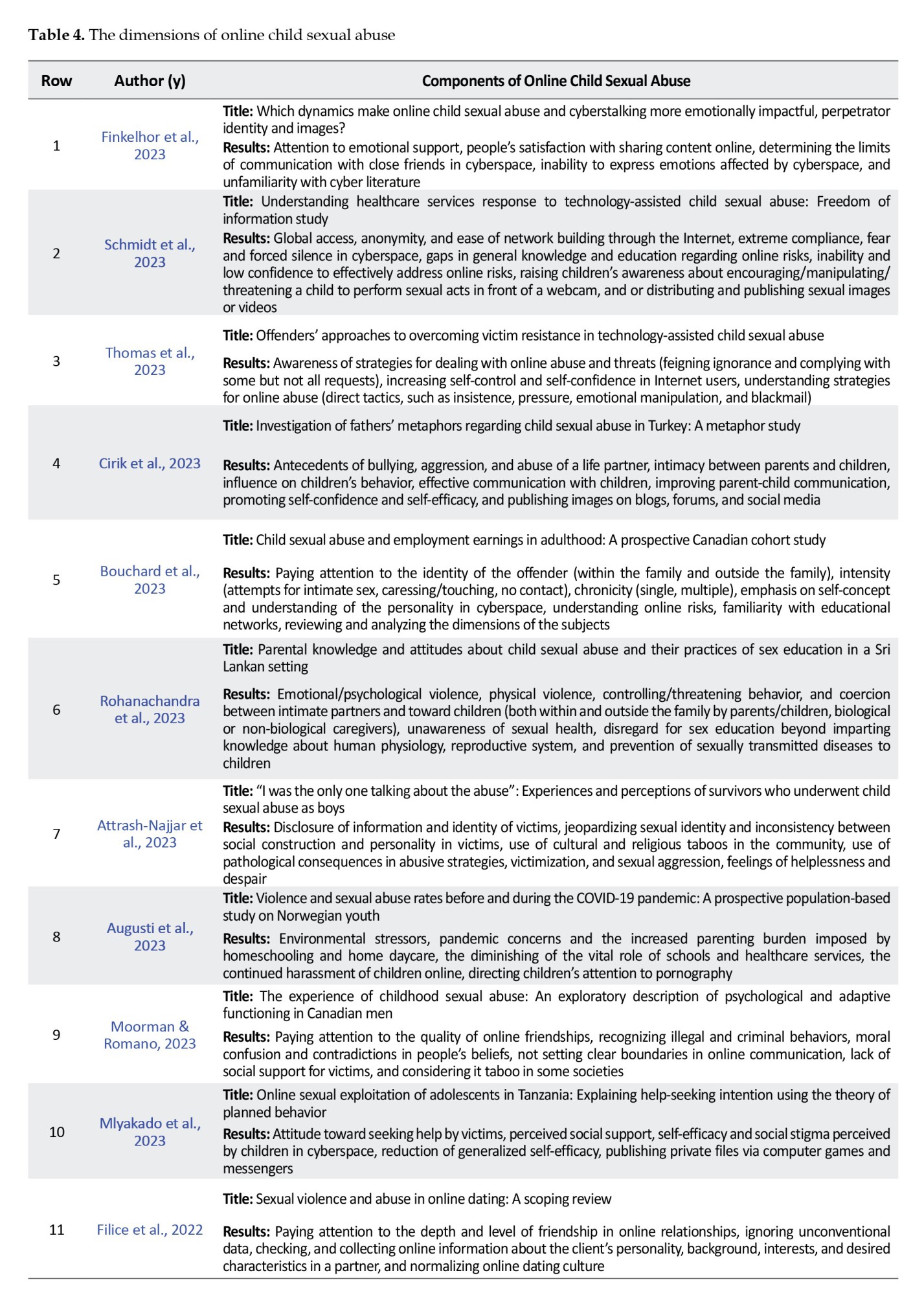
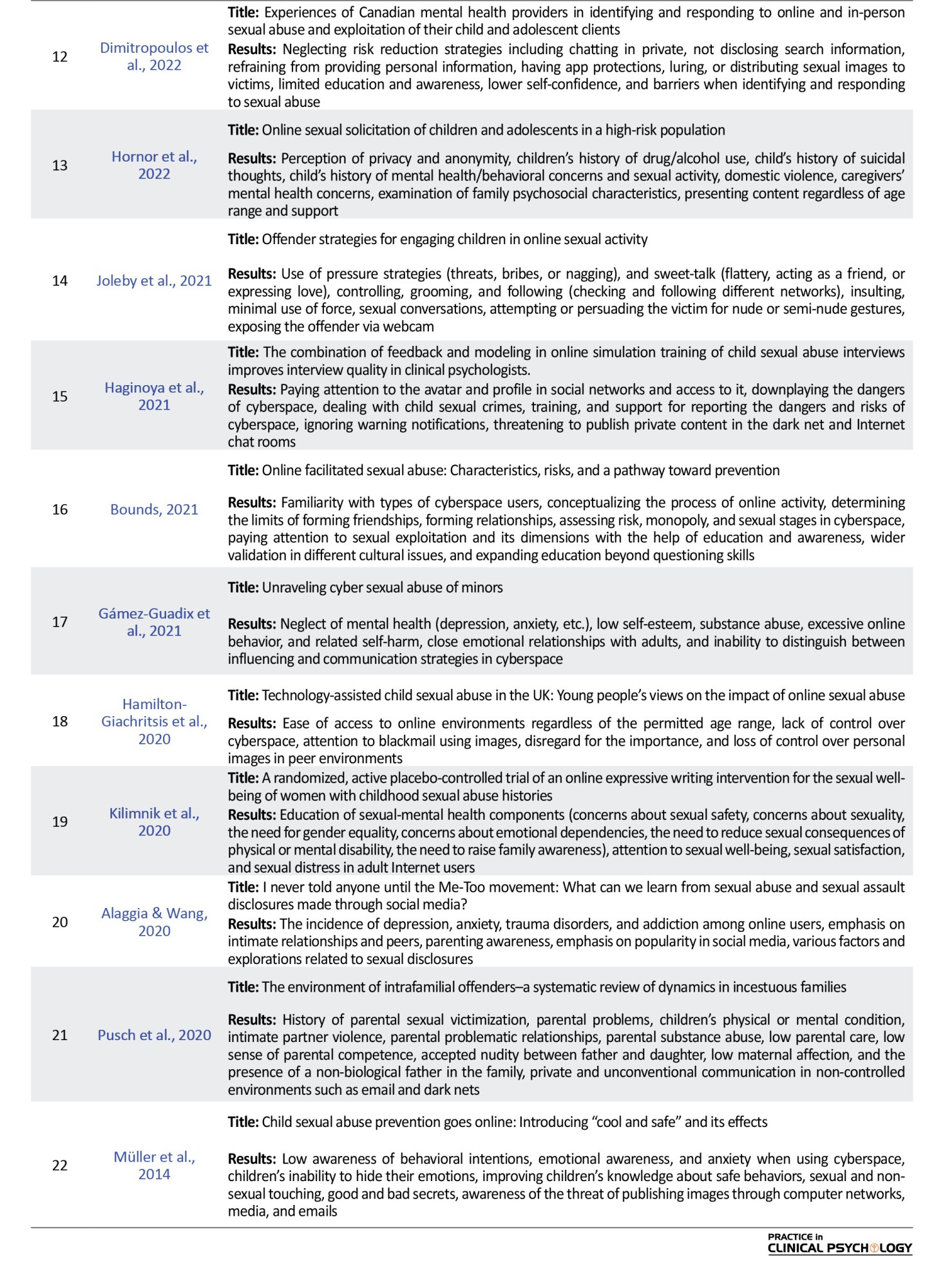
The dimensions of online child sexual abuse were extracted through open coding from the selected articles as detailed in Table 4.
Step 7: Reporting the results
This systematic review was conducted to reveal the components of online child sexual abuse. First, all components were identified through open coding. Afterward, all scientific findings were integrated to come up with a solid understanding of the components of online child sexual abuse. Then, the extracted open codes were recoded and the overlapping codes and those with a similar meaning were merged into axial codes. Finally, the analysis of the resulting codes revealed that online child sexual abuse could be explained by four dimensions (selective codes) as detailed in Table 5.


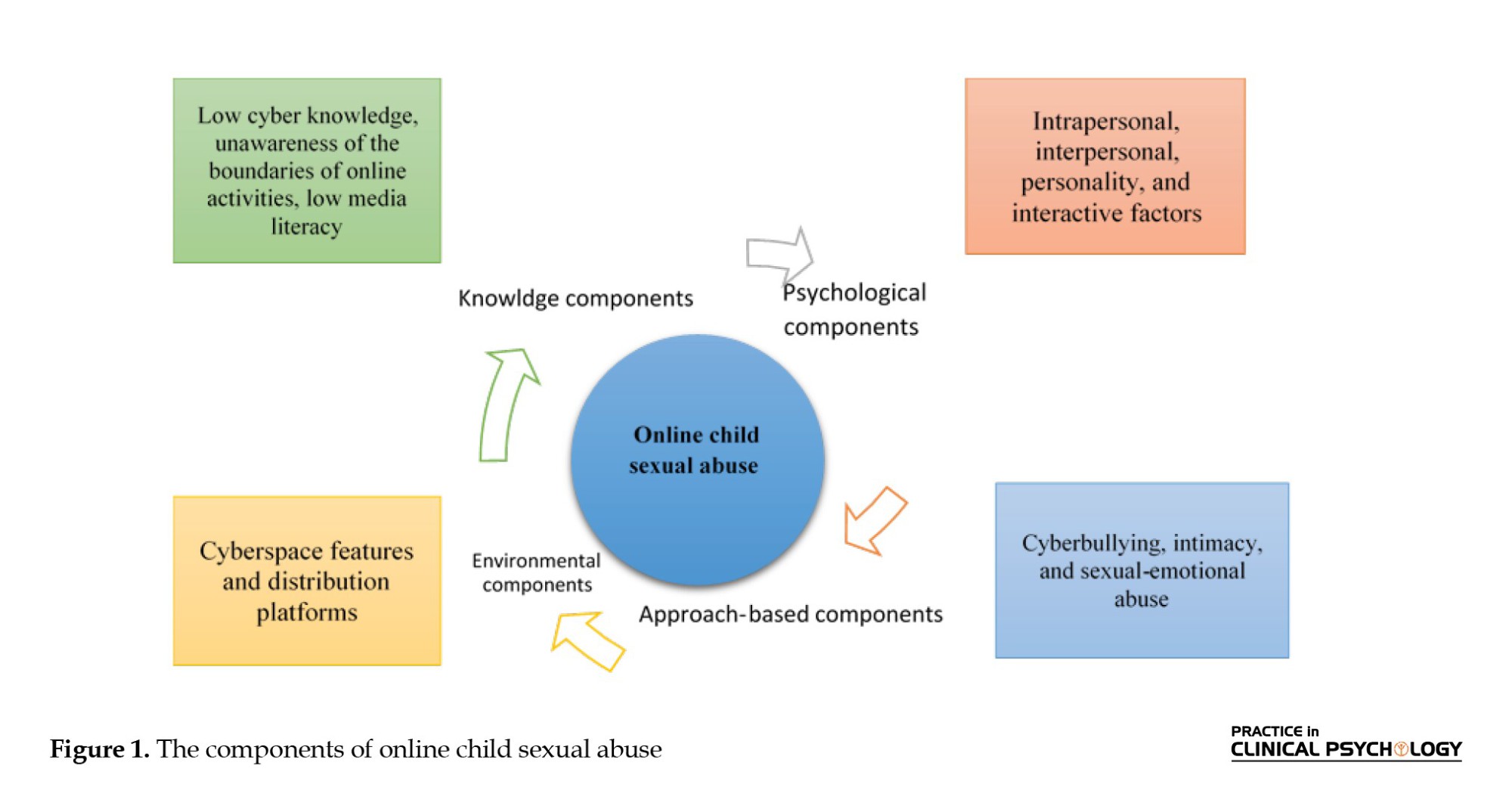
Figure 1 displays the components of online child sexual abuse. As can be seen, all the components are non-linearly interrelated, affecting each other.
Discussion
The growing rate of online sexual abuse cases in the 21st century has become a major problem that has attracted the attention of many researchers around the world. Hence, many studies have addressed this phenomenon. To this end, the present study provided a systematic review of the previous studies in the literature on online child sexual abuse. The results revealed 4 dimensions of online child sexual abuse, including knowledge components, psychological components, approach-based components, and environmental components, as discussed below.
Knowledge components of online child sexual abuse are related to children’s unawareness of cyberspace boundaries and the lack of knowledge required for analyzing online opportunities. Moreover, low cyber knowledge is rooted in an unawareness or partial awareness of the functions of online networks and data protection techniques in online media and platforms. In addition, children’s unawareness of cyberspace complexities, cyber ethics, and the impacts of online media on other aspects of their lives can contribute to online sexual abuse as highlighted in previous studies (Alaggia & Wang, 2020; Bounds, 2021). These researchers reported that awareness of online networks and their impacts is one of the main factors underlying cyber abuse and victimization. Furthermore, the present study showed the failure to identify the boundaries in online dating and relationships, the inability to evaluate cyberspace risks, the failure to distinguish between good and bad secrets when communicating with adults, and the inability to make a distinction between influencing and communication strategies in online platforms can facilitate online child sexual abuse, as confirmed in the literature (Hornor et al., 2022; Moorman & Romano, 2023). The third knowledge component was low media literacy because it is essential to pay attention to the current actions and the requirements of the current era for a better understanding of media analysis and cyberspace activities. Low media literacy is related to the unawareness of methods used to analyze internet input information, unawareness of active educational media and platforms, unawareness of ethical principles governing social networks, the failure to understand the goals and consequences of online messages, inability to analyze opportunities in cyberspace and assess their validity, and weak critical and reflective thinking. These results were consistent with the results reported in the literature (Augusti et al., 2023; Hornor et al., 2022).
Psychological factors, including intrapersonal and extra-personal characteristics of children, can increase the risk of online sexual abuse. Moreover, children with low self-confidence, disrupted self-concept, anxiety and worry, emotional concealment, trauma disorders, and emotional dependence on friends in cyberspace are more likely to be victims of online sexual abuse, as highlighted in previous studies (Finkelhor et al., 2023; Thomas et al., 2023; Joleby et al., 2021). Moreover, interpersonal characteristics, including an emotional detachment from family members, accepted nudity at home, the failure to control cyberspace and extreme freedom, support for reporting cyberspace risks, history of traumatic thoughts (suicide, etc.), disregard for the intensity of friendship in online relationships, normalization of online dating culture, and low intimacy in parent-child interactions can contribute to ineffective and counterproductive interactions in online media and networks as confirmed by previous studies in the literature (Haginoya et al., 2021; Dimitropoulos et al., 2022; Finkelhor et al., 2023).
Approach-based components, including cyberbullying strategies, intimacy strategies, and emotional-sexual abuse refer to the techniques used by offenders to abuse and extort children in cyberspace. Cyberbullying involves threatening to notify parents, threatening to expose nude and semi-nude images, online extortion through psychological pressure on the child, frequent child abuse through different communication networks, exploiting or encouraging a child to engage in sexually inappropriate behaviors, and ignoring the child’s needs for interaction, leading to online child sexual abuse (Schmidt et al., 2023; Cirik et al., 2023; Filice et al., 2022). Emotional-sexual intimacy and abuse involve manipulating children’s innocent feelings consistent with criminals’ sexually destructive goals. Accordingly, verbal flattery, hostile verbal humiliation, concerns about victims’ social desires, grooming children to perform sexual acts preferred by the offender, gaining trust through the victim’s desired online communication, sexual exploitation by making the child interested in pornography, and the offender’s flattery and expression of love by pretending to be a friend can increase the risk of online sexual abuse in children, as confirmed in the literature (Gámez-Guadix et al., 2021; Cirik et al., 2023).
Previous studies also indicated that environmental factors, such as an insecure and shared environment, providing various accesses to users in online network platforms (webcam, microphone, etc.), disabling notifications and alerts, the failure to provide age-appropriate content, disregard for malware, lack of support from security services for the online environment can contribute to increasing the risk of online child sexual abuse (Dimitropoulos et al., 2022; Hornor et al., 2022). In addition, the platforms used for producing and sharing sexual content, such as websites, dark nets, forums, social media, instant messaging, internet chat rooms, peer-to-peer networks, and computer games can increase the risk of online child sexual abuse (Cirik et al., 2023, Haginoya et al., 2021; Müller et al., 2014).
Conclusion
Addressing cyberspace risks for learners can reduce the possibility of online sexual abuse. The present study sought to extract factors contributing to online child sexual abuse in previous studies. The insights from this study can be helpful for educational administrators and cyberspace managers to develop programs or adopt strategies to reduce the risk of online sexual abuse in Iranian children. This study was conducted with some shortcomings, including the unavailability of studies on online sexual abuse in Iranian children and difficulty accessing related databases. In line with the results of the study, the following suggestions are offered:
Cyber, media, and sexual literacy should be incorporated into educational curricula for students. Moreover, online sexual education should be provided for children and adolescents, especially during the post-COVID-19 period through training courses and workshops.
Parents and teachers should pay attention to children’s self-confidence and emotional dependence on online, social media and platforms. They can also provide some training on online sexual abuse and how to prevent it.
A safe virtual environment should be developed for children using artificial intelligence technologies and biometric authentication tools. Besides, children’s awareness needs to be raised using educational platforms and they should have access to websites with content fitting their age requirements.
Parents should establish effective emotional relationships with their children. They should also receive some education about parenting styles and effective parent-child interactions.
Ethical Considerations
Compliance with ethical guidelines
This study approved by Faculty of Humanities and Social Sciences, Tehran North Branch, Islamic Azad University, Tehran, Iran (Code: IR.IAU.TNB.REC.1402.036).
Funding
This study was extracted from the PhD. dissertation of Hadi Gholamrezaei, approved by the Faculty of Humanities and Social Sciences, Tehran North Branch, Islamic Azad University , Tehran, Iran.
Authors' contributions
All authors equally contributed to preparing this article.
Conflict of interest
The authors declared no conflict of interest.
References
The rapid development of communication technologies, along with the widespread use of the Internet, has fundamentally transformed almost every part of human life, including work, health, education, communication, and entertainment, to the extent that these technologies have become a common basic need for human daily life due to their relatively low cost and easy access (Cikman et al., 2017). With the widespread use of the Internet, commercial sites that contain pornographic content, chat rooms, and uncontrolled communication networks serve as platforms that connect children with pedophiles, thereby promoting potential online sexual abuse (Keçe, 2018). Sex offenders often use the Internet to communicate with children to facilitate in-person sexual abuse or to create and distribute sexual images of children (Dimitropoulos et al., 2022). Online child sexual abuse includes displaying, collecting, compiling, and distributing child sexual abuse content for personal sexual gratification, financial gain, interaction with other pedophiles, participation in online live streams of child sexual abuse, and grooming to encourage children to engage in sexual acts online and then offline and in reality (Özçalık & Atakoğlu, 2021; Açar, 2017). Child grooming refers to a relationship based on trust between a minor and an adult who uses information and communication technologies to solicit and exploit young people to provide online and offline child sexual abuse acts (Kloess et al., 2014).
Child sexual abuse material has become a big problem in the 21st century, and despite the increased awareness and efforts of governments and non-governmental organizations in the private sector, still alarming statistics exist in this field. In 1998, the US National Center for Missing and Exploited Children identified online sexual abuse as a new form of child sexual abuse. In the following year, 9 673 reports were received by this center, and in 2021, these reports reached >29 million reports, of which 99% were related to online child sexual abuse, indicating a three-thousand-fold increase over the past 22 years (IWF, 2020). Sex offenders often use the Internet to communicate with children to facilitate in-person sexual abuse or to create and distribute sexual images of children (Dimitropoulos et al., 2022). Online sexual solicitation (OSS) of children occurs when an adult stranger uses the Internet to access, interact, and establish relationships with children to induce them to engage in sexual conversations and acts, offline and/or online. Online sexual solicitation may involve a variety of sexually explicit acts, desired or undesired by the child, such as initiating conversations of a sexual nature (e.g. cybersex, describing sexual acts, and exchanging sexual information), exchanging pornographic images, and meeting offline and engaging in sexual acts (Gemara et al., 2022). Various studies have addressed the effect of experiencing physical abuse, sexual and emotional abuse, and physical and emotional neglect in children in the etiology of mental disorders in children (McNally et al., 2021; McKay et al., 2021; Marshall et al., 2020) and have shown that many factors, including cyberspace and its widespread use, are effective in the phenomenology of child abuse (Drăgan, 2018). However, the reported cases of child sexual abuse are like the tip of the iceberg as the exact rate of sexual abuse is not stated in detail. For example, Abbas and Jabeen (2020) showed that 44% of the men and 39% of the women participating in the study reported that they have experienced at least one form of sexual abuse (looking at private parts, pornography, touching private parts, talking sexually and or having sex) in childhood.
As stated earlier, online child abuse has been addressed by many studies conducted in the last few years. Since children start using the Internet at a young age and for a long time, they are at risk of engaging in online sexual abuse and these online threats pose a potentially growing problem to the mental health of the community, leading to a dramatic increase in child abuse reports. Accordingly, the Internet Watch Foundation (IWF), a UK-based NGO, identified >153,000 new web pages containing child sexual abuse images in 2020, showing a 16% increase compared to 2019 (IWF, 2020). In the UK in 2016, 100000 people were involved in online sexual abuse, and 5%-25% of children in Europe and the US experienced sexual abuse, viewed pornography, and became involved in online sexual abuse. Moreover, from 2009 to 2013, four thousand child victims of sexual abuse were identified by the Interpol (Carr, 2020). Acar also reported that during 10 weeks, more than a thousand different people offered money to a virtual Filipino child named Sweetie, so that in exchange for receiving this money, he would send them online sexual images of himself. Landberg et al. (2022) showed that 27.5% of high school students, including 40.5% of females and 12.8% of males in Sweden with an average age of 18 have engaged in online sex or been forced to do so in the past year.
Thus, it is essential to raise the awareness of parents, psychologists, counselors, teachers, and all health professionals dealing with children and families about online child sexual abuse. To this end, this systematic review study seeks to review the studies conducted in this field to reveal the dimensions of online child sexual abuse highlighted in the literature in recent years. The insights from this study can contribute to developing child sexual abuse prevention and training programs.
Materials and Methods
Using a systematic review approach, the present study was conducted to analyze studies that addressed online child sexual abuse. Systematic review is a standard approach to examining the questions and findings of several studies (Boland et al., 2014). A systematic review is an explicit method to identify, evaluate, and analyze the previous work done by researchers and scholars (Okoli & Schabram, 2010). Studies that can be evaluated using a systematic review should be published online and present field and empirical findings. Thus, the research setting includes all valid scientific articles addressing online child sexual abuse. Since sexual abuse on online platforms has increased in recent years, all the selected articles were conducted within this time frame (2014-2023). The required data were collected using a researcher-made worksheet form. The identified scientific documents and records were categorized using content analysis. The collected data were analyzed using open, axial, and selective coding and Wright et al.’s seven-step model (Wright et al., 2007). To assess the reliability of the coding scheme, the data were re-coded by four raters using Scott’s method. The inter-rater agreement was estimated as 0.74, showing a 74% agreement between the raters (Equation 1).
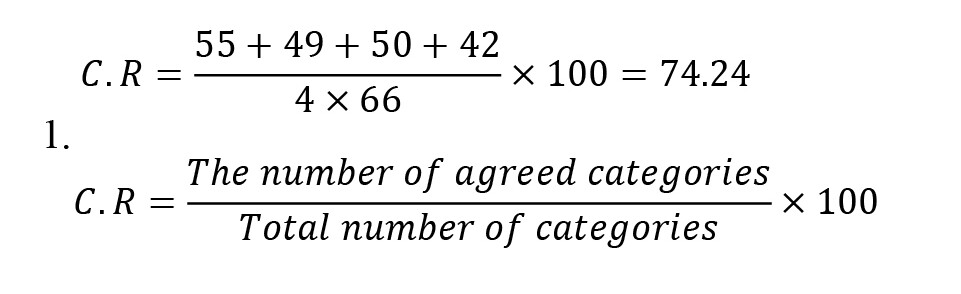
This study was conducted through five steps as detailed below:
Step 1: Developing the research question
Table 1 presents the research questions.

Step 2: Formulating the research protocol
To reduce any probable bias, the review protocol was developed before retrieving the related records. To collect the data, we developed a set of criteria to select and categorize the articles (Moffet, 2015).
A. The inclusion criteria used in this study included:
1. The articles that addressed learners’ online sexual abuse
2. The articles that reported adequate data (the sum of data or information required to create an influential contention or back a specific conclusion) on online child sexual abuse
3. The full-text articles that were reviewed by subject-matter experts and published online
B. The exclusion criteria used in this study included:
1. The articles that did not report enough data about online child sexual abuse or the articles that only assessed the relationship between online child sexual abuse and other variables quantitatively
2. The articles lacked scientific rigor and were published in low-quality journals and conferences without an international index or reported impact factor.
3. The articles that were not published in the intended time frame (2014-2023). In other words, the articles that were published before 2014 and their results were no longer useful for current issues.
Step 3: Search strategy
The intended articles were searched using the search strategy proposed by Prashar (2015). To this end, all valid scholarly articles were searched using the keywords “child sexual abuse”, “online child sexual abuse”, and “cyber sexual abuse” in domestic databases, such as Google, SID, Normagas, Magiram, Comprehensive Humanities Portal, Iranian Research Institute for Information Science and Technology (IranDoc), and Elmnet Search Engine as well as international databases including Scopus, Emerald, Sage, Scientific Information Database, Science Direct, ProQuest, Springlink, World Scientific, Taylor & Francis, Google Scholar, Eric, and Wiley. The records related to the objectives of the study were retained and unrelated records were removed. Furthermore, Google Scholar and related websites, such as Child Abuse & Neglect were searched manually to identify the gray literature. To improve the rigor of the results, the databases were searched separately by two experts who were familiar with search methods and information sources. Moreover, three experts in the field of online platforms and psychology monitored the search protocol. The data in this study were collected from scholarly and research articles published in national and international databases. The articles have been published using strict review protocols in reputed journals.
Step 4: Extracting articles
A standard form was used to record the intended information, including the source (journal name, article title, and author(s)), purpose (the objective(s) of the study), methodology, and results. The data were collected by searching the intended keywords in the databases. Considering the inclusion criteria, 113 articles published in English and Persian were identified. After reviewing the articles based on the exclusion criteria, the irrelevant articles were excluded and finally, 22 articles were used for the final review. Table 2 presents the search strategy used in this study.

Step 5: Quality assessment
Every study, including qualitative studies and systematic reviews, must have acceptable validity and objectivity. In systematic review studies, a comprehensive search will lead to finding a lot of relevant studies, but since all these studies are not of adequate and acceptable quality, before the review, the extracted records should be selected following the inclusion and exclusion criteria. Before entering the analysis, each article should be analyzed using suitable tools and based on defined criteria, and only articles that have acceptable quality should be analyzed and reviewed. A checklist was used in this study to specify the high, medium, and low quality of the selected articles. To this end, the selected articles were scored and those with lower scores were excluded. Table 3 presents a rating checklist developed based on Carlsen et al.’s model (Carlsen et al., 2008).
The extracted articles were reviewed and rated independently by at least two raters using the criteria detailed in Table 3. The raters specified the reasons to reject an article. However, in the case of any disagreement between the two raters, the article would be reviewed and assessed by a third rater.

Results
Data analysis was performed using Wright et al.’s seven-step model (Wright et al., 2007).
Step 6: Data analysis
The dimensions of online child sexual abuse were extracted through open coding from the selected articles as detailed in Table 4.


Step 7: Reporting the results
This systematic review was conducted to reveal the components of online child sexual abuse. First, all components were identified through open coding. Afterward, all scientific findings were integrated to come up with a solid understanding of the components of online child sexual abuse. Then, the extracted open codes were recoded and the overlapping codes and those with a similar meaning were merged into axial codes. Finally, the analysis of the resulting codes revealed that online child sexual abuse could be explained by four dimensions (selective codes) as detailed in Table 5.


Figure 1 displays the components of online child sexual abuse. As can be seen, all the components are non-linearly interrelated, affecting each other.

Discussion
The growing rate of online sexual abuse cases in the 21st century has become a major problem that has attracted the attention of many researchers around the world. Hence, many studies have addressed this phenomenon. To this end, the present study provided a systematic review of the previous studies in the literature on online child sexual abuse. The results revealed 4 dimensions of online child sexual abuse, including knowledge components, psychological components, approach-based components, and environmental components, as discussed below.
Knowledge components of online child sexual abuse are related to children’s unawareness of cyberspace boundaries and the lack of knowledge required for analyzing online opportunities. Moreover, low cyber knowledge is rooted in an unawareness or partial awareness of the functions of online networks and data protection techniques in online media and platforms. In addition, children’s unawareness of cyberspace complexities, cyber ethics, and the impacts of online media on other aspects of their lives can contribute to online sexual abuse as highlighted in previous studies (Alaggia & Wang, 2020; Bounds, 2021). These researchers reported that awareness of online networks and their impacts is one of the main factors underlying cyber abuse and victimization. Furthermore, the present study showed the failure to identify the boundaries in online dating and relationships, the inability to evaluate cyberspace risks, the failure to distinguish between good and bad secrets when communicating with adults, and the inability to make a distinction between influencing and communication strategies in online platforms can facilitate online child sexual abuse, as confirmed in the literature (Hornor et al., 2022; Moorman & Romano, 2023). The third knowledge component was low media literacy because it is essential to pay attention to the current actions and the requirements of the current era for a better understanding of media analysis and cyberspace activities. Low media literacy is related to the unawareness of methods used to analyze internet input information, unawareness of active educational media and platforms, unawareness of ethical principles governing social networks, the failure to understand the goals and consequences of online messages, inability to analyze opportunities in cyberspace and assess their validity, and weak critical and reflective thinking. These results were consistent with the results reported in the literature (Augusti et al., 2023; Hornor et al., 2022).
Psychological factors, including intrapersonal and extra-personal characteristics of children, can increase the risk of online sexual abuse. Moreover, children with low self-confidence, disrupted self-concept, anxiety and worry, emotional concealment, trauma disorders, and emotional dependence on friends in cyberspace are more likely to be victims of online sexual abuse, as highlighted in previous studies (Finkelhor et al., 2023; Thomas et al., 2023; Joleby et al., 2021). Moreover, interpersonal characteristics, including an emotional detachment from family members, accepted nudity at home, the failure to control cyberspace and extreme freedom, support for reporting cyberspace risks, history of traumatic thoughts (suicide, etc.), disregard for the intensity of friendship in online relationships, normalization of online dating culture, and low intimacy in parent-child interactions can contribute to ineffective and counterproductive interactions in online media and networks as confirmed by previous studies in the literature (Haginoya et al., 2021; Dimitropoulos et al., 2022; Finkelhor et al., 2023).
Approach-based components, including cyberbullying strategies, intimacy strategies, and emotional-sexual abuse refer to the techniques used by offenders to abuse and extort children in cyberspace. Cyberbullying involves threatening to notify parents, threatening to expose nude and semi-nude images, online extortion through psychological pressure on the child, frequent child abuse through different communication networks, exploiting or encouraging a child to engage in sexually inappropriate behaviors, and ignoring the child’s needs for interaction, leading to online child sexual abuse (Schmidt et al., 2023; Cirik et al., 2023; Filice et al., 2022). Emotional-sexual intimacy and abuse involve manipulating children’s innocent feelings consistent with criminals’ sexually destructive goals. Accordingly, verbal flattery, hostile verbal humiliation, concerns about victims’ social desires, grooming children to perform sexual acts preferred by the offender, gaining trust through the victim’s desired online communication, sexual exploitation by making the child interested in pornography, and the offender’s flattery and expression of love by pretending to be a friend can increase the risk of online sexual abuse in children, as confirmed in the literature (Gámez-Guadix et al., 2021; Cirik et al., 2023).
Previous studies also indicated that environmental factors, such as an insecure and shared environment, providing various accesses to users in online network platforms (webcam, microphone, etc.), disabling notifications and alerts, the failure to provide age-appropriate content, disregard for malware, lack of support from security services for the online environment can contribute to increasing the risk of online child sexual abuse (Dimitropoulos et al., 2022; Hornor et al., 2022). In addition, the platforms used for producing and sharing sexual content, such as websites, dark nets, forums, social media, instant messaging, internet chat rooms, peer-to-peer networks, and computer games can increase the risk of online child sexual abuse (Cirik et al., 2023, Haginoya et al., 2021; Müller et al., 2014).
Conclusion
Addressing cyberspace risks for learners can reduce the possibility of online sexual abuse. The present study sought to extract factors contributing to online child sexual abuse in previous studies. The insights from this study can be helpful for educational administrators and cyberspace managers to develop programs or adopt strategies to reduce the risk of online sexual abuse in Iranian children. This study was conducted with some shortcomings, including the unavailability of studies on online sexual abuse in Iranian children and difficulty accessing related databases. In line with the results of the study, the following suggestions are offered:
Cyber, media, and sexual literacy should be incorporated into educational curricula for students. Moreover, online sexual education should be provided for children and adolescents, especially during the post-COVID-19 period through training courses and workshops.
Parents and teachers should pay attention to children’s self-confidence and emotional dependence on online, social media and platforms. They can also provide some training on online sexual abuse and how to prevent it.
A safe virtual environment should be developed for children using artificial intelligence technologies and biometric authentication tools. Besides, children’s awareness needs to be raised using educational platforms and they should have access to websites with content fitting their age requirements.
Parents should establish effective emotional relationships with their children. They should also receive some education about parenting styles and effective parent-child interactions.
Ethical Considerations
Compliance with ethical guidelines
This study approved by Faculty of Humanities and Social Sciences, Tehran North Branch, Islamic Azad University, Tehran, Iran (Code: IR.IAU.TNB.REC.1402.036).
Funding
This study was extracted from the PhD. dissertation of Hadi Gholamrezaei, approved by the Faculty of Humanities and Social Sciences, Tehran North Branch, Islamic Azad University , Tehran, Iran.
Authors' contributions
All authors equally contributed to preparing this article.
Conflict of interest
The authors declared no conflict of interest.
References
Abbas, S. S., & Jabeen, T. (2020). Prevalence of child abuse among the university students: a retrospective cross-sectional study in University of the Punjab, Pakistan. International Quarterly of Community Health Education, 40(2), 125-134. [DOI:10.1177%2F0272684X19861578.] [PMID]
Açar, K. V. (2017). Organizational aspect of the global fight against online child sexual abuse. Glob Policy; 8, 259-62. [DOI:10.1111/1758-5899.12418]
Alaggia, R., & Wang, S. (2020). I never told anyone until the me-too movement”: What can we learn from sexual abuse and sexual assault disclosures made through social media? Child Abuse & Neglect, 103, 104312. [DOI:10.1016/j.chiabu.2019.104312] [PMID]
Attrash-Najjar, A., Cohen, N., Glucklich, T., & Katz, C. (2023). “I was the only one talking about the abuse”: Experiences and perceptions of survivors who underwent child sexual abuse as boys. Child Abuse & Neglect, 140, 106144. [DOI:10.1016/j.chiabu.2023.106144] [PMID]
Augusti, E. M., Myhre, M. C., Wentzel-Larsen, T., & Hafstad, G. S. (2023). Violence and sexual abuse rates before and during the COVID-19 pandemic: A prospective population-based study on Norwegian youth. Child Abuse & Neglect, 136, 106023. [DOI:10.1016/j.chiabu.2023.106023] [PMID]
Carr, A., Duff, H., & Craddock, F. (2020). A systematic review of reviews of the outcome of noninstitutional child maltreatment. Trauma, Violence, & Abuse, 21(4), 828-843. [DOI:10.1177/1524838018801334]
Cherry, G., Dickson, R., & Boland, A. (2017). Doing a systematic review: A student’s guide. California: Sage. [Link]
Bouchard, S., Langevin, R., Vergunst, F., Commisso, M., Domond, P., & Hébert, M., et al. (2023). Child sexual abuse and employment earnings in adulthood: A prospective Canadian cohort study. American Journal of Preventive Medicine, 65(1), 83–91. [DOI:10.1016/j.amepre.2023.01.040] [PMID]
Bounds, D. (2021). Online facilitated sexual abuse: Characteristics, risks, and a pathway toward prevention. Journal of the American Academy of Child & Adolescent Psychiatry, 60(10), 80. [DOI:10.1016/j.jaac.2021.07.337]
Çıkman, B., Salman, Ö., & Çalışkan, D. (2017). [Adı: Meraklı, soyadı: çocuk, durum: Çevrimiçi, sonuç: Grooming, internette çocuk istismarı (Turkish)]. The Journal of Current Pediatrics; 15(3), 87-97. [Link]
Cirik, V. A., Aksoy, B., & Bulut, E. (2023). Investigation of fathers’ metaphors regarding child sexual abuse in Turkey: A metaphor study. Journal of Pediatric Nursing, 72, e210–e216.[DOI:10.1016/j.pedn.2023.06.030] [PMID]
Dimitropoulos, G., Lindenbach, D., Devoe, D. J., Gunn, E., Cullen, O., & Bhattarai, A., et al. (2022). Experiences of Canadian mental health providers in identifying and responding to online and in-person sexual abuse and exploitation of their child and adolescent clients. Child Abuse & Neglect, 124, 105448.[DOI:10.1016/j.chiabu.2021.105448] [PMID]
Dimitropoulos, G., Lindenbach, D., Devoe, D. J., Gunn, E., Cullen, O., & Bhattarai, A., et al. (2022). Experiences of Canadian mental health providers in identifying and responding to online and in-person sexual abuse and exploitation of their child and adolescent clients. Child Abuse & Neglect, 124, 105448. [DOI:10.1016/j.chiabu.2021.105448] [PMID]
Drăgan, A. T. (2018). Child pornography and child abuse in cyberspace. Journal of Legal Studies, 21(35), 52-60. [Link]
Filice, E., Abeywickrama, K. D., Parry, D. C., & Johnson, C. W. (2022). Sexual violence and abuse in online dating: A scoping review. Aggression and Violent Behavior, 67, 101781. [DOI:10.1016/j.avb.2022.101781]
Finkelhor, D., Turner, H., & Colburn, D. (2023). Which dynamics make online child sexual abuse and cyberstalking more emotionally impactful: Perpetrator identity and images? Child Abuse & Neglect, 137, 106020. [DOI:10.1016/j.chiabu.2023.106020] [PMID]
Gámez-Guadix, M., De Santisteban, P., Wachs, S., & Wright, M. (2021). Unraveling cyber sexual abuse of minors: Psychometrics properties of the Multidimensional Online Grooming Questionnaire and prevalence by sex and age. Child Abuse & Neglect, 120, 105250. [DOI:10.1016/j.chiabu.2021.105250] [PMID]
Gemara, N., Cohen, N., & Katz, C. (2022). “I do not remember… You are reminding me now!”: Children’s difficult experiences during forensic interviews about online sexual solicitation. Child Abuse & Neglect, 134, 105913. [DOI:10.1016/j.chiabu.2022.105913] [PMID]
Haginoya, S., Yamamoto, S., & Santtila, P. (2021). The combination of feedback and modeling in online simulation training of child sexual abuse interviews improves interview quality in clinical psychologists. Child Abuse & Neglect, 115, 105-113. [DOI:10.1016/j.chiabu.2021.105013] [PMID]
Hamilton-Giachritsis, C., Hanson, E., Whittle, H., Alves-Costa, F., & Beech, A. (2020). Technology-assisted child sexual abuse in the UK: Young people’s views on the impact of online sexual abuse. Children and Youth Services Review, 119, 105451. [DOI:10.1016/j.childyouth.2020.105451]
Hornor, G., Billa, A., Daniels, A., Ibrahim, A., Landers, T., & Prince, C., et al. (2022). Online sexual solicitation of children and adolescents in a high-risk population. Journal of Pediatric Health Care, 36(5), 449-456. [DOI:10.1016/j.pedhc.2022.04.010] [PMID]
IWF. (2020). IWF annual report 2020: Face the facts. Cambridge: Internet Watch Foundation (IWF). [Link]
Joleby, M., Lunde, C., Landström, S., & Jonsson, L. S. (2021). Offender strategies for engaging children in online sexual activity. Child Abuse & Neglect, 120, 105214. [DOI:10.1016/j.chiabu.2021.105214] [PMID]
Keçe, H. (2018). [Social anciety level of girl's children for sexual excessive victims living in children's support centers (Turkish)] [MSc. thesis]. Ankara: Hacettepe Üniversitesi Sosyal Bilimler Enstitüsü. [Link]
Kilimnik, C., McMahon, L., & Meston, C. (2020). A randomized, active placebo-controlled trial of an online expressive writing intervention for the sexual well-being of women with childhood sexual abuse histories. The Journal of Sexual Medicine, 17(3), 233. [DOI:10.1016/j.jsxm.2020.04.266]
Kloess, J. A., Beech, A. R., & Harkins, L. (2014). Online child sexual exploitation: Prevalence, process, and offender characteristics. Trauma, Violence & Abuse, 15(2), 126–139.[DOI:10.1177/1524838013511543] [PMID]
Landberg, Å., Svedin, C. G., & Jonsson, L. S. (2022). Patterns of disclosure and perceived societal responses after child sexual abuse. Child Abuse & Neglect, 134, 105914. [DOI:10.1016/j.chiabu.2022.105914] [PMID]
Marshall, C., Semovski, V., & Stewart, S. L. (2020). Exposure to childhood interpersonal trauma and mental health service urgency. Child Abuse & Neglect, 106, 104464. [DOI:10.1016/j.chiabu.2020.104464] [PMID]
McKay, M. T., Cannon, M., Chambers, D., Conroy, R. M., Coughlan, H., & Dodd, P., et al. (2021). Childhood trauma and adult mental disorder: A systematic review and meta-analysis of longitudinal cohort studies. Acta Psychiatrica Scandinavica, 143(3), 189–205. [DOI:10.1111/acps.13268] [PMID]
McNally, P., Taggart, L., & Shevlin, M. (2021). Trauma experiences of people with an intellectual disability and their implications: A scoping review. Journal of Applied Research in Intellectual Disabilities : JARID, 34(4), 927–949. [DOI:10.1111/jar.12872] [PMID]
Mlyakado, B. P., Li, J. C. M., & Jia, C. X. (2023). Online sexual exploitation of adolescents in Tanzania: Explaining help-seeking intention using the theory of planned behavior. Children and Youth Services Review, 154, 107-129. [Link]
Moffet, J. (2015). Twelve tips for “flipping” the classroom. Medical Teacher, 37(4), 331-336. [DOI:10.3109/0142159X.2014.943710] [PMID]
Moorman, J., & Romano, E. (2023). The experience of childhood sexual abuse: An exploratory description of psychological and adaptive functioning in Canadian men. Child Abuse & Neglect, 145, 106-122. [DOI:10.1016/j.chiabu.2023.106402] [PMID]
Müller, A. R., Röder, M., & Fingerle, M. (2014). Child sexual abuse prevention goes online: Introducing “cool and safe” and its effects. Computers & Education, 78, 60-65. [DOI:10.1016/j.compedu.2014.04.023]
Okoli, C., & Schabram, K. (2010). A guide to conducting a systematic literature review of information systems research. Sprouts: Working Papers on Information Systems, 10(26). [Link]
Özçalık, C. K., & Atakoğlu, R. (2021). Online child sexual abuse: Prevalence and characteristics of the victims and offendersJournal of Psychiatric Nursing, 12, 76-81. [Link]
Prashar, A. (2015). Assessing the flipped classroom in operations management: A pilot study. Journal of Education for Business, 90(3), 126-38. [DOI:10.1080/08832323.2015.1007904]
Pusch, S. A., Ross, T., & Fontao, M. I. (2021). The environment of intrafamilial offenders-A systematic review of dynamics in incestuous families. Sexual Offending: Theory, Research, and Prevention, 16, 1-20. [DOI:10.5964/sotrap.5461]
Rohanachandra, Y. M., Amarakoon, L., Alles, P. S., Amarasekera, A. U., & Mapatunage, C. N. (2023). Parental knowledge and attitudes about child sexual abuse and their practices of sex education in a Sri Lankan setting. Asian Journal of Psychiatry, 85, 103623. [DOI:10.1016/j.ajp.2023.103623] [PMID]
Schmidt, F., Bucci, S., & Varese, F. (2023). Understanding healthcare services response to technology-assisted child sexual abuse: A freedom of information study. Child Abuse & Neglect, 143, 106323. [DOI:10.1016/j.chiabu.2023.106323] [PMID]
Type of Study: Review paper |
Subject:
Rehabilitation
Received: 2023/12/15 | Accepted: 2024/02/12 | Published: 2024/07/1
Received: 2023/12/15 | Accepted: 2024/02/12 | Published: 2024/07/1
| Rights and permissions | |
 |
This work is licensed under a Creative Commons Attribution-NonCommercial 4.0 International License. |